Dev Update #3: Anti-DDoS Spoofing Incidents
Tamer

Since our last development update, we have been working hard to be able to provide our members with even more unique and revolutionary features. The features implemented in this update will result in a cleaner peering LAN and might send ripples across the internet.
Distributed denial of service (DDoS) attacks are becoming a mainstream problem for the internet and they are mostly fought back retroactively using anti-DDoS companies and scrubbing centers. We believe everything should be done to prevent them from being executed in the first place, proactively. As an internet exchange, we can not step in and start dropping malicious packets, as this would most certainly cause undesirable effects, so we are doing what we can to help create awareness leading to the prevention of potential DDoS attacks.
Spoofing Incidents
The internet consists of a large amount of (mostly) collaborating networks, however, due to the sheer amount of networks and people involved, there is a chance for configuration errors or mistakes to creep in. One of the more dangerous problems which could be caused by this is IP spoofing, which is a key component to perform reflection (amplification) Distributed Denial of Service (DDoS) attacks.
In order to cause awareness and ensure we do our part to make the internet a better place, we inform our customers about such activities by keeping track of where configuration issues may be present. On request, notifications are enabled, where members will receive a notification in case malicious activities have been detected on their port.
Please keep in mind that this service is not a replacement for firewalls and good practices, it exists solely to indicate where they might be a problem with the configuration of the aforementioned measures.
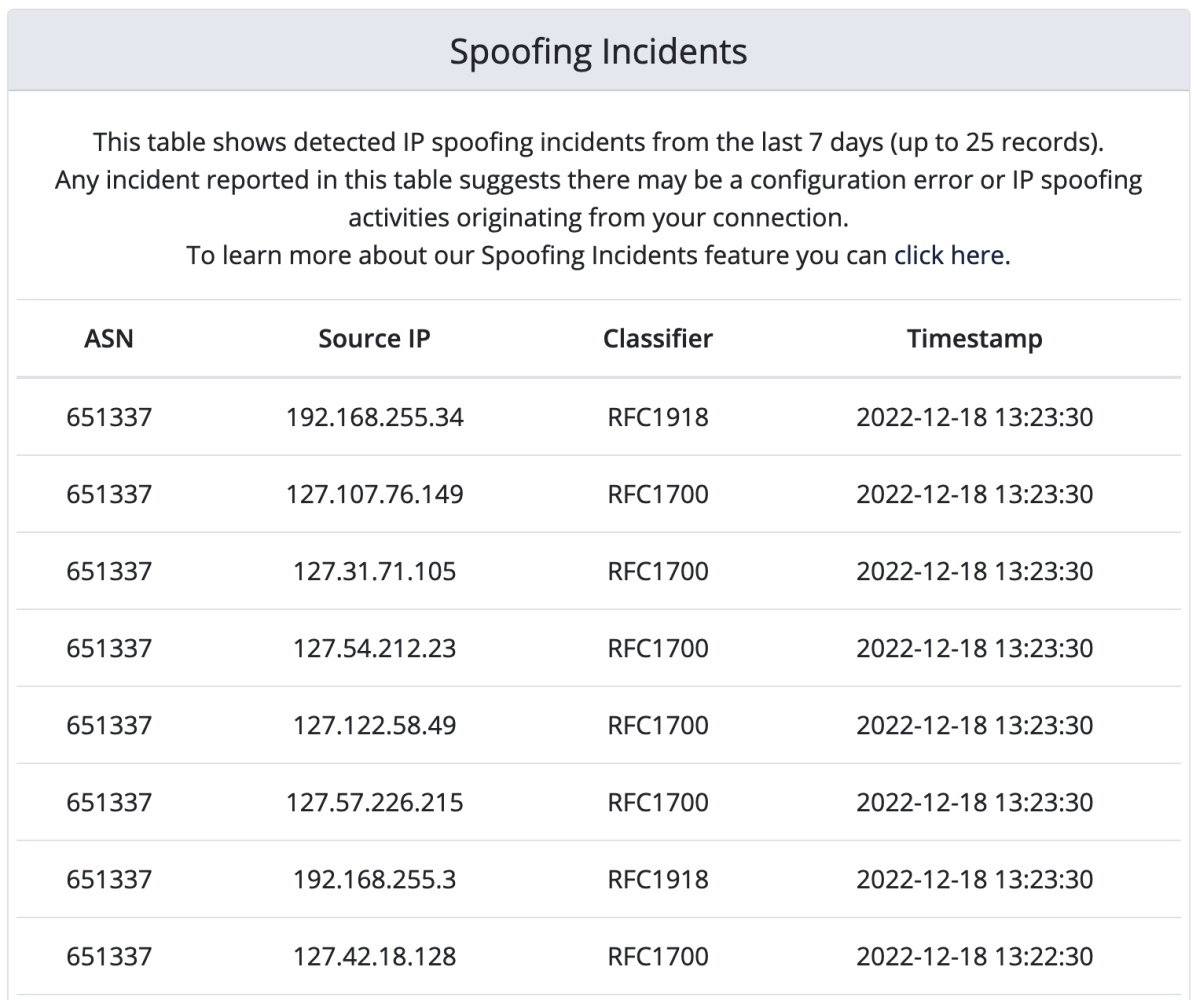
These statistics can be viewed in our customer portal and will show what our system triggered on. To provide this service we do not look at the contents of the packets (the contents of the packets are truncated for this purpose), so unfortunately we are not able to provide any further inside as to what might be causing the trouble. However, if you are stuck trying to identify the source, as a member you can get in touch and we will try to be of assistance.
You can read more (including the classifiers we use) about this feature on our website.
ARP Suppression Stage 2
As of recently, members may have noticed a large drop in the total amount of broadcast traffic. One member noticed this and brought it up to us, along with the following screenshot:
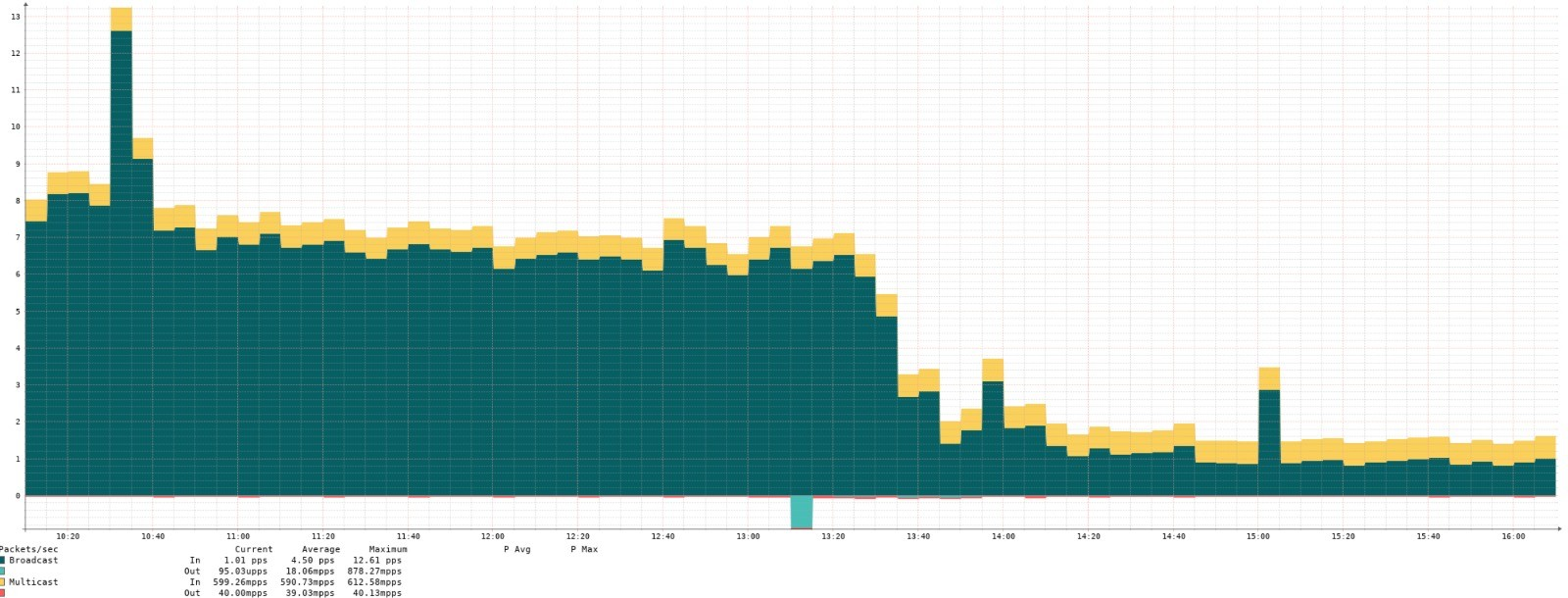
For us, peering LAN hygiene is very important to creating a reliable and efficient environment for our members to exchange traffic in. For this, we have further improved our ARP suppression systems which now reduces the number of ARP packets flying across the peering LAN to a bare minimum.
Thank you for reading and for your time!